As we reach the one‑year mark since the NIS2 transposition deadline (17 October 2024), many businesses are still navigating uneven national implementations across the EU. Despite differences in timing, the direction of travel is clear: if your organization falls within the scope, regulators expect concrete, documented cybersecurity risk management, incident reporting, and governance. This article explains what organizations are in scope, what obligations and sanctions look like, and the practical steps to take now.
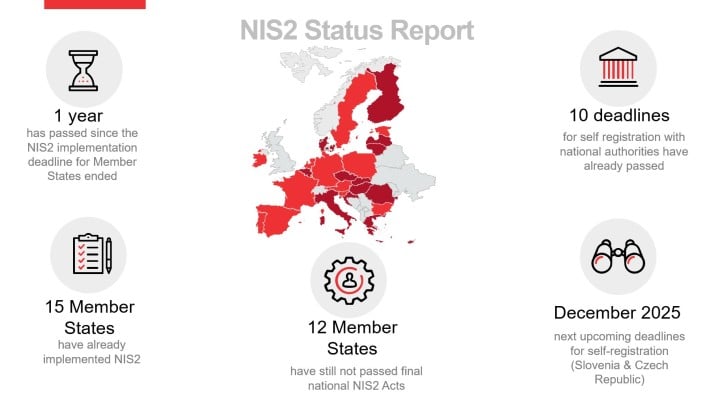
Member States have advanced at different speeds: some already enforce registration and supervision, others are finalizing national laws or national decrees.
The practical takeaway: do not wait for a local “go‑live” date. Even in jurisdictions without a final transposition, companies should urgently begin implementing their NIS2 strategy and not allow themselves to be paralyzed by the existing uncertainties. Depending on the company structure and existing cybersecurity standards, extensive measures are necessary that cannot be implemented overnight.
Scope: Who is caught by NIS2?
NIS2 significantly widens the net compared to the 2016 NIS regime. It covers “essential” and ‘important’ entities across 18 sectors, ranging from energy, transport, health and digital infrastructure to postal and courier services, waste management, chemicals, food production and a broad array of ICT and managed service providers. Size matters: as a rule of thumb, medium and large entities in those sectors are in scope, with certain exceptions (for example, DNS providers).
Two practical points are often overlooked: (i) internal IT or shared services within a corporate group can trigger in‑scope status (for example, a parent company providing group IT to EU subsidiaries); and (ii) NIS2 applies extraterritorially to non‑EU providers offering covered services in the EU.
Ancillary activities generally covered
NIS2 does not provide a general exception for ancillary business activities, which adds complexity for companies with diverse operations. While certain thresholds exist – such as in the wastewater sector, where activities are only covered if essential to the entity’s general business activities – national implementation approaches vary significantly. For example, Germany’s NIS2 Draft Act introduced a general exception for activities deemed “negligible” compared to overall business operations. In contrast, the Belgian and Italian supervisory authorities each clarified in their FAQs that ancillary activities can trigger NIS2 application unless the law provides exemptions for specific activities. Austria’s latest Draft Act similarly lacks a general exception; however, for selected business activities, the regulation is only triggered if it constitutes the “main business activity” e.g. for electricity production. These differences underscore the need for multinational groups to adopt not only a group-wide NIS2 compliance strategy but also tailored national assessments.
Core obligations: Registration, risk management, supply chain security and incident reporting
NIS2 requires a defensible, risk‑based security program backed by leadership oversight. In practice, boards must approve the cybersecurity strategy and can be held personally accountable for persistent non‑compliance. Key obligations include:
- Registration: In most jurisdictions, in‑scope entities must conduct a NIS2 self-assessment and actively register with the national authority.
- Risk management measures: These measures include policies on risk analysis and information system security, business continuity (e.g. backup management) and disaster recovery, secure development and change management, and maintenance, including vulnerability handling and disclosure. Furthermore, organizations must establish policies and procedures regarding the use of cryptography and, where appropriate, encryption, implement multi-factor authentication or continuous authentication solutions, and adopt measures for human resources security and access control policies, including asset management.
- Supply chain security: Regulated entities cover supply chain security, including security-related aspects concerning relationships with direct suppliers or service providers, build minimum contractual controls, and ensure that procurement and vendor governance reflect the “all‑hazards” approach.
- Incident reporting: Regulated entities must submit an early warning within 24 hours of becoming aware of a significant incident; an update within 72 hours; and a final report within one month (or earlier, if the incident is resolved).
Consequences
NIS2 gives authorities a broad supervision toolbox. Beyond audits and remediation orders, fines can be significant: up to EUR 10 million or 2% of the worldwide annual turnover (whichever is higher).
Financial exposure is only part of the picture. In certain sectors, repeated or serious breaches can also lead to temporary bans for managers, temporary designation of a monitoring officer, and temporarily suspend certifications or authorizations concerning parts of the relevant business activities.
Additional complexity for multinational groups
Developing an effective NIS2 strategy for multinational groups is particularly challenging due to the directive’s structural characteristics. NIS2 applies at the entity level, not the group level, which makes individual assessments for each entity essential. The directive also contains complex jurisdictional rules, meaning a single entity may fall under the national NIS2 laws of multiple Member States. As NIS2 follows the minimum harmonization principle, national implementations can differ significantly in scope and obligations, adding another layer of complexity.
Multinational companies often need to register with more than one national NIS2 authority, making it crucial to establish a comprehensive compliance strategy before the first registration. This challenge is compounded by the fact that many Member States have yet to finalize their implementation laws.
Practical next steps
It is essential for multinational groups to closely monitor legislative developments across all the jurisdictions in which they operate. Several local registration deadlines have already passed, and a few more are scheduled for later this year. To minimize exposure, it is vital to design a group-wide NIS2 strategy before starting the national registration processes.
National companies operating in jurisdictions without a final NIS2 transposition must act quickly too. NIS2 introduces extensive obligations, the implementation of which requires time, resources, and collaboration between a number of internal and external stakeholders. With skill, uncertainties due to lacking national transposition can be navigated, enabling fundamental questions to be clarified and strategies to be developed before the national law comes into force. Organizations that wait until the last moment to begin the process will probably not be able to complete it in time.