In Brief
Businesses subject to New York State’s Department of Financial Services’ (“DFS”) “Cybersecurity Requirements for Financial Services Companies” (23 CRR-NY 500 )(“Part 500”), which was recently amended, should take note of several new requirements that came into effect on May 1, 2025. Part 500 includes some of the most detailed cybersecurity regulations in the nation and DFS has an active enforcement program against alleged violations of Part 500. The newly effective provisions will impose significant additional network security obligations on financial institutions and other organizations regulated by DFS.
Business Classification under Part 500
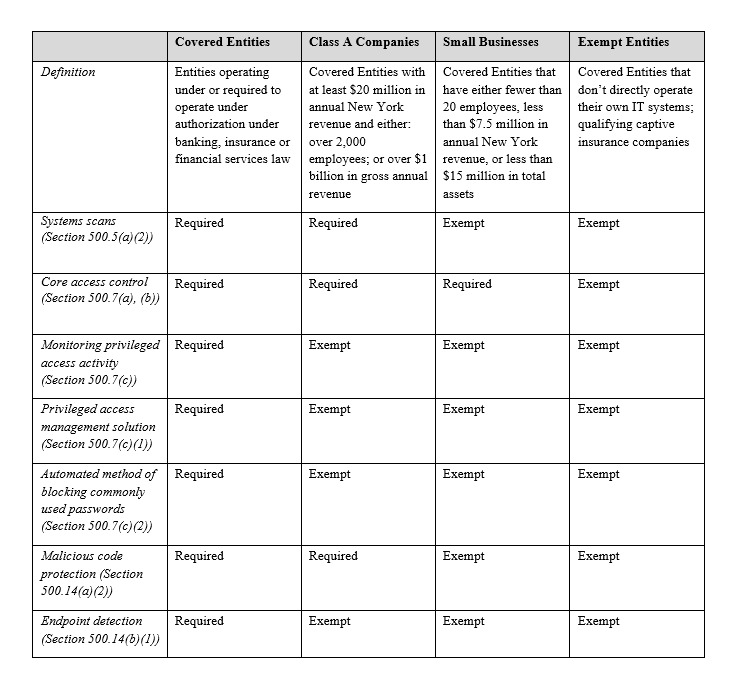
Preparing for compliance with Part 500 begins by understanding how your organization is classified by DFS and determining which requirements flow from this classification. Part 500 mandates different requirements depending on the type of organization, with the regulation distinguishing among “Covered Entities”, “Class A” businesses, and exempt businesses.
Part 500 defines a “Covered Entity” as one operating under or required to operate under a license, registration, charter, certificate, permit, accreditation or similar authorization under [New York banking, insurance or financial services law].”
“Class A” companies are Covered Entities with at least $20 million in gross annual revenue in each of the last two fiscal years from business operations of the covered entity and its affiliates in New York and either:
- over 2,000 employees averaged over the last two fiscal years, including employees of both the covered entity and all of its affiliates no matter where located; or
- over $1 billion in gross annual revenue in each of the last two fiscal years from all business operations of the covered entity and all of its affiliates.
Covered Entities that do not meet certain criteria are exempt from some of Part 500’s obligations. For example, Covered Entities that have either fewer than 20 employees, less than $7.5 million in annual New York revenue, or less than $15 million in total assets are subject to reduced requirements (“Small Businesses”). Covered Entities that don’t directly operate their own IT systems are relieved of all obligations discussed below (“Exempt Entities”).
Upcoming Part 500 Requirements
The way Part 500 classifies your organization will determine which of the new requirements apply. The newly applicable requirements fall broadly into three categories:
- System scans (Section 500.5(a)(2))
- Access controls (Section 500.7)
- Endpoint detection and protection against malicious code (Section 500.14)
System Scans: Under Section 500.5(a)(2), Covered Entities must conduct automated scans of their information systems for the purpose of discovering, analyzing, and reporting vulnerabilities. Covered Entities should also undertake manual scans of systems that aren’t covered by automated scanning. Part 500 does not specify how frequently system scans must occur—rather, the frequency is to be determined by the Covered Entity’s risk assessment. Small Businesses and Exempt Entities are not required to conduct system scans.
Access Controls: Part 500’s access control requirements consist of several provisions, whose applicability depends on the type of entity.
The following core requirements apply both to Covered Entities and Small Businesses:
- Access privileges: Access privileges to systems that provide access to nonpublic information must be limited to those necessary to perform a user’s job.
- Privileged accounts: The number of privileged accounts—in other words, accounts that can perform security-relevant functions—must be limited and the access functions must also be limited to what is necessary for the user to perform their job. Use of privileged accounts should also be limited to when the user is performing a function requiring privileged account access.
- Review: Access privileges should be reviewed at least annually and accounts and access that are no longer needed should be removed or disabled.
- Remote control protocols: Protocols that enable the remote control of devices should be either be disabled or configured securely.
- Termination of access: Access for departing employees or contractors must be disabled promptly.
- Password policy: If passwords are used for authentication, a written policy that meets industry standards must be implemented.
In addition to the above requirements, Class A companies must monitor privileged access activity and implement a privileged access management solution and an automated method to block common passwords, to the extent feasible.
Part 500’s access control obligations do not apply to Exempt Entities.
Endpoint Detection and Protection Against Malicious Code: Sections 500.14(a)(2) and 500.14(b) also come into effect and require Covered Entities to protection against malicious code and perform endpoint detection, respectively. Under Section 500.14(a)(2), a Covered Entity’s controls must include those that monitor and filter web traffic and electronic mail to block malicious content. Class A companies must also practice endpoint detection to monitor for anomalous network activity (such as lateral movement within an environment) and implement centralized logging and security event alerting. The Class A company’s CISO may however approve the use of reasonably equivalent or more secure technologies. Sections 500.14(a)(2) and 500.14(b) do not apply to Small Businesses and Exempt Entities.
Next Steps
To ensure comprehensive compliance with these new requirements, businesses must coordinate among legal, risk management, and information security functions. This collaboration is crucial for addressing the multifaceted aspects of cybersecurity, from legal obligations to technical safeguards. Consulting with knowledgeable cybersecurity counsel will further enhance a company’s ability to navigate the complexities Part 500 to implement a security program that is both compliant and resilient.
The DFS requirements should also be considered in the broader context of cybersecurity regulation, with a growing number of states and federal agencies mandating proactive measures. These range from California’s draft regulations requiring annual cybersecurity audits, to data privacy laws like Tennessee’s that explicitly link compliance to established security frameworks like the NIST Risk Management Framework, to the Securities & Exchange Commission requirements on cybersecurity program disclosures, to the forthcoming CIRCIA rules. While these laws and regulations share the common aim of strengthening cybersecurity practices across critical sectors, special care is required to determine what specific requirements apply to your organization and to design and implement an integrated compliance program around those specific requirements.
Annex: Overview of May 1, 2025 Part 500 Requirements